
Selling Security: Web Exposure Reports
How to use the Web Exposure Report to approach prospects, close sales and boost your MRR
Now, heads up: this article is long. If you’re in a rush, we’ve included a TL;DR below. When able, you should carve out 10 minutes to read it in full. It’ll help you understand the strategies our Partners use to generate leads, book sales meetings and improve sales conversions with Web Exposure Reports (WER) - and up-sell existing clients, too!
The Web Exposure Report (WER) is a potent tool for demonstrating an organization's vulnerability to phishing - the most common way cybercriminals launch attacks.
The decision-makers at many organizations have heard about Phishing and Ransomware in the news, but they don’t know where to start or how to judge their own risk. This is where the WER comes in. With this report, you’ll demonstrate that the threat is very real and provide ways your prospect can avoid becoming a hacker’s next victim.
As is often the case, prevention is infinitely better than cure.
TL;DR on WER Reports:
- Hop into your Sales Enablement portal on the INFIMA Dashboard.
- Generate Teaser/Preview Report: Input your prospect’s domain name to create a preview of their Full Web Exposure Report - free of any sensitive information
- Send Teaser: Send this preview with your first outreach message. (we’ve conveniently included a template in your Dashboard) Your angle should be to arrange a face-to-face or phone appointment where you will present the full version of the report.
- Book your meeting!
- Present Full WER: Walk your prospect through each section of the Report. These include background on the phishing threat, the publicly available data that the report has pulled from the Internet and Dark Web and an explanation of your Security Awareness Training Solution.
- Explain The Threat: The full WER includes sensitive information like: names, email addresses and job roles. Explain how this information is used by hackers.
Example: when a hacker has the name and email address of the Accounts Payable Manager, a phishing message can be sent under the guise of a supplier payment to coax your employee right into the hacker’s net.
- Provide Case Studies: There are case studies on INFIMA’s blog that you can use to demonstrate the relevance of phishing attacks to your prospect’s organization. This helps them understand that they, too, are targets.
- Ask Questions: Encourage your prospect to think about the consequences of an attack like these on their organization when you provide real-world examples.
- Up-Sell: You can also use the WER to upsell additional controls beyond security awareness training - O365/GSuite migration, antivirus, spam filtering and MFA all play a part in countering the threat of phishing attacks.
- Close: INFIMA’s Partners get per user per month pricing, and onboarding is a breeze.
Start selling!
Ok, now let's take a deeper dive...
The Web Exposure Report
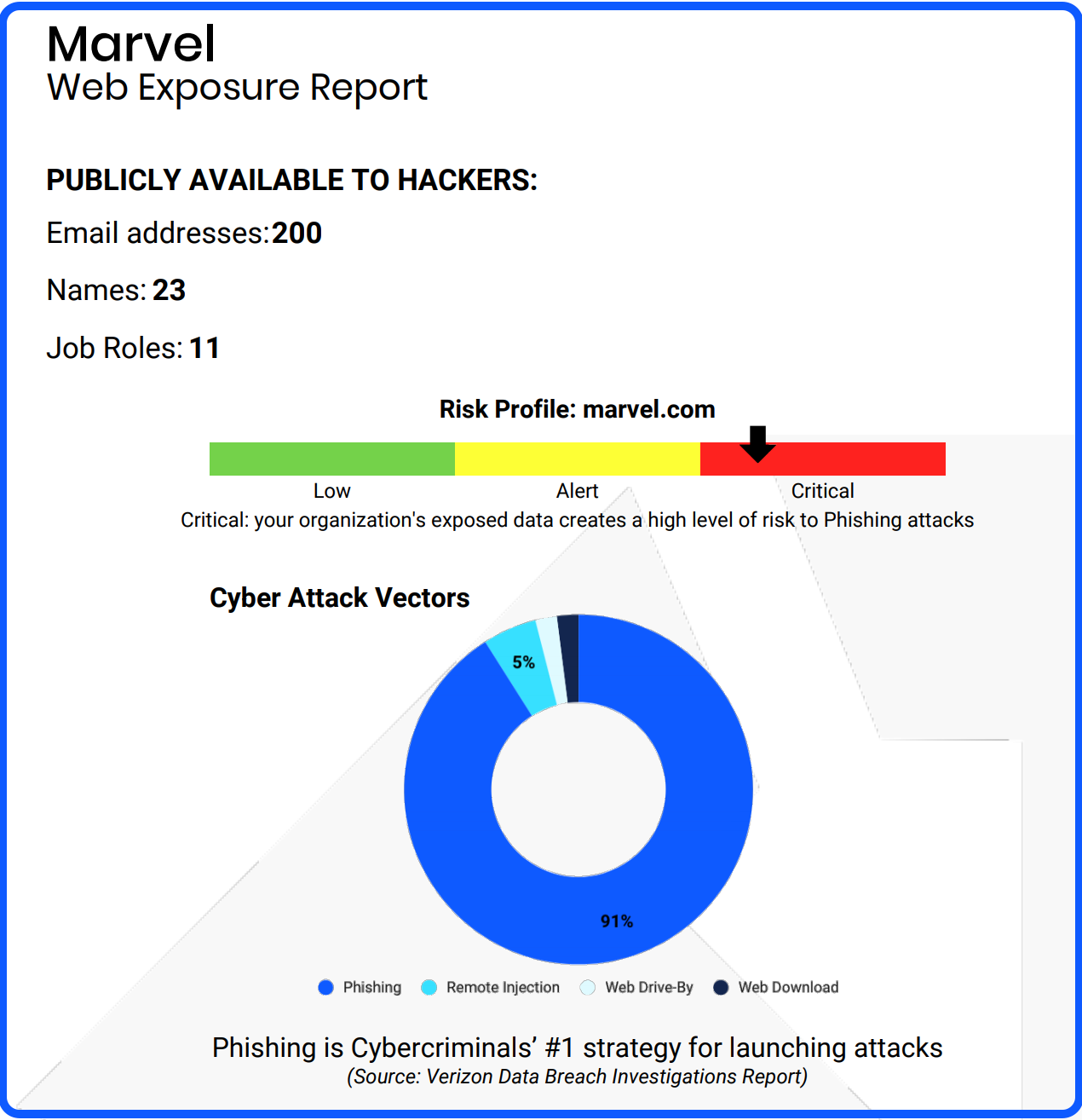
Web Exposure Reports can be generated for any given domain name and present a list of associated staff names, email addresses and job roles that can be found online (both on the indexed Internet and the Dark Web).
The WER provides context to phishing attacks and their real-world implications for an organization, helping C-suite managers understand their real-time risks. The report further shares the protective benefits of deploying regular Security Awareness Training (SAT) and Phish Testing.
The steps laid out below are intended as guidance and are based around feedback from Partners who have had success with this process.
If you choose to use the report in other ways, we’d love to hear how it goes!
Booking a Meeting:
The first step before approaching potential clients with WER is to generate a Teaser/Preview Report from the Sales Enablement portal on your INFIMA Dashboard.
Action Step 1: Input your prospect’s email domain.
The Teaser Report gives a “headline summary” of the information held within the full WER, without revealing any sensitive information.
Action Step 2: Send the Teaser Report to your prospect
We provide a targeted outreach template (yep - right in the INFIMA Dashboard!) to accompany the WER Teaser, presenting your prospect with information specific to their organization and creating an “open loop.” Your prospect can only close this loop by responding to your message and booking a time to learn more!
The Teaser Report captures the attention of your prospect in a way that shows you have invested resources into identifying a weakness within their organization and freely offered the findings of your research. In the spirit of reciprocity, this approach greatly improves the response rate to cold outreach messages.
Depending on your preference and your proximity to your prospect’s offices, the WER Teaser can be sent with an invitation to arrange an in-person meeting or a video call where you’ll present the full Web Exposure Report.
Action Step 3: Book your meeting!
In a culture where there are always voices and distraction vying for attention, presenting the full WER in person (or at least over video call) allows you to highlight the relevance of the Report’s contents and provide context to the information. It also gives you the opportunity to answer any questions that your prospect may have and respond to any objections they might raise (more on these later).
Presenting The Full Web Exposure Report
The WER is deliberately structured to provide context for your prospect, so that they are able to connect the dots between the information within the report and the risk to their organization from phishing attacks.
Action Step 4: Create and review your prospect’s Full WER
The Opener:
The first page of the report provides the context and reinforces how easily the information can be scraped by automated software. This data collection process is effortless for the attackers. Once armed with this information, phishing is a numbers game - they can send thousands of targeted messages every day. They only need one click in a phishing email to initiate an attack.
Often hackers operate from regions outside of US jurisdiction, making it extremely difficult to prosecute the senders of Phishing emails. This is why it is so important that your prospect’s employees are able to recognize phishing threats and respond appropriately. Your prospect should understand that this isn’t a problem which can readily be solved with law enforcement.
The Results:
The second part of the WER lists the publicly available names, emails addresses and job roles of individuals in your prospect’s organization, all pulled from the Internet and Dark Web in seconds.
At this point in your conversation, it is important to explain to your prospect why having this information together can allow an attacker to form a very convincing angle of attack within a phishing message.
Let's take two examples.
Example 1:
An attacker has the name, email address and job titles of staff within the finance department. A phishing email can now be sent to a junior member of the finance department by name, pretending to be from a supplier. This message claims that an invoice is overdue and must be settled promptly to avoid penalty fees. A handy link or attachment within the email will allow them to view and satisfy the invoice in question. This seems perfectly normal in that person’s day-to-day duties, and they will be understandably quick to investigate further. They click to see the details of the invoice in question. And the attacker is in. This breach most often results in ransomware encrypting files and servers, and a hefty payment being requested to release them. While this is going on, the organization loses virtually all of its IT systems, meaning staff can’t work and customers can’t be served. Business is at a standstill.
Example 2:
Next up, let's say the cybercriminal finds the contact information of the HR manager. A LinkedIn message is crafted to look as though it comes from a recruiter. The “recruiter” suggests they have a very promising position open, and it fits this employee’s background perfectly. This seems a totally reasonable connection request The curious HR manager clicks the “Connect” link in the email, and the attacker is in. The cybercriminal can install its malicious payload with just a click. The attacker can begin with stealing passwords and data to later hold for ransom.
There are numerous case studies on the INFIMA blog which detail phishing attacks on organizations in many industries, from hospitals and schools to law firms and asset managers. You can use these to demonstrate the threat that exists to your prospect’s organization and the importance of having protective measures in place.
Action Step 5: Ask questions!
When presenting these examples, encourage your prospect to consider what the impact would look like on their own business if they were in this position:
- Have they experienced a Ransomware or cyber attack?
- How would a complete loss of IT services affect them?
- Could they continue to serve customers without network access?
- How much would their reputation suffer from the publishing of stolen data from their network?
Closing Your Sale with Security Awareness Training
The final part of the WER focuses on the effectiveness of Security Awareness Training in combating the phishing threat.
After you’ve presented the WER to your prospect, they should see the threat that exists from phishing emails and will better understand the potential consequences of a breach.
Action Step 6: Present your solutions!
The next step is to present your solutions to the problem. We’ll focus on Security Awareness Training for the purposes of this post.
Controls are only as strong as the humans operating them - 90% of successful cyber attacks begin with a phishing email. This means that 90% of cyber attacks can be prevented if the end-user is aware of the threat, knows what to look for and reacts appropriately.
This statistic alone is a powerful incentive for an organization to invest in training their team.
The chart included in the WER uses actual client data to illustrate the improvement in security awareness within organizations delivering SAT to their staff..
Overcoming Objections
Objections to training vary greatly, which is why it is important to focus primarily on the effectiveness of INFIMA’s training delivery. As a managed solution, the prospect will gain the following benefits:
- Regular training delivered by email to all staff. The courses take under 10 minutes to complete and include a short quiz at the end to boost retention of the material by the trainee.
- Training content includes industry-specific compliance modules directly relevant to the organization.
- Rapid onboarding - complete in just 10 minutes.
- New employees are automatically enrolled as they join the organization.
- In addition to Training courses, Phish testing emails are regularly sent to test awareness. If an employee clicks, they are given immediate feedback, along with additional learning opportunities.
- The program results are delivered in concise monthly reports. These reports invariably highlight risky users so that their weakness can be directly addressed.
- Each organization is provided with a custom Security Awareness Training policy. This document allows the organization to demonstrate their commitment to security to their stakeholders, regulators and customers.This also makes audits a breeze, with all of the evidence of training in one place.
- INFIMA bills Partners per user per month, so your client never has to pay for unused licenses.
Action Step 7: Close the deal
At this stage in your conversation with the prospect, you’ll want to move to close your new client! You may want to present other parts of your package, but know that you can always up-sell once you’ve got your foot in the door.
The Bottom Line
We want to help you sell more security programs.
We’re continuing to develop tools to make our Partners lives as easy as possible, cutting the time required to run your security awareness program so you can keep growing your business!
It's time to sell. Let's Go!
INFIMA Security Newsletter
Join the newsletter to receive the latest updates in your inbox.






