
Hackers use our minds against us...
Hackers con even the most savvy IT professionals with Phishing emails. Why do we fall for these tricks?
You've told your team how dangerous Phishing and Ransomware are for your organization.
You've trained employees on what to look for.
You've had your executive team send out warning messages.
Heck, you've probably discussed this until you're blue in the face!
Yet, your people keep clicking on Phishing emails.
What if it's not entirely about knowledge?
What if behaviors play a key role in avoiding (or falling for) these attacks?
Behavioral Science
Much of the scourge of Phishing boils down to behavioral science. Nerds like us over here dive deep into the remarkable research in the field to see how we can use behavioral insights for protecting you and your team.
One of our all-time favorite brains in this space (and we're not alone!) is Danny Kahneman. I mean, he won a Nobel prize for his work! So yeah, we're not the first to realize his brilliance (and that of his now-deceased colleague, Amos Tversky).
In Thinking, Fast and Slow, Kahneman reshaped the way behavioral science is viewed and applied to everyday life. We've learned a lot from him and others in the field.
Ok so back to cybersecurity and Phishing. We take the best of the behavioral sciences and apply behavioral solutions to cybersecurity.
Loss Aversion
A key learning from behavioral research focuses on cognitive biases. We all have them.
Don't believe me? Let's do a quick thought experiment...
Let's say I just gave you $100 (theoretically!). Now, you can either take that cool, crisp Benji and walk away, OR you can flip a coin.
If the coin comes up heads, you get another $150. But if it comes up tails, you have to give me back the $100, plus another $50 out of your own pocket.
Kahneman's research showed that otherwise rational people overwhelmingly choose to take the $100 and get on their way, even though the "rational" person should be indifferent to the two options. This concept is called loss aversion.
Let's review:
Option A (no coin toss)- expected value is $100 (because it's a $100 bill!)
Option B (coin toss) - expected value is also $100 (either +$250 or -$50)
The expected value in both scenarios is $100, but humans have a distaste for taking losses (ahem.. stock portfolios anyone??).
Ok, now that you've agreed (or disagreed with me), let's apply this to security.
Cognitive Bias and Cybercrime
Unfortunately, hackers can also use these tools to manipulate our decision making.
Let's look at some examples:
Loss Aversion
You get an email that says you must change your password or lose 4 email messages. Seems crazy, right....
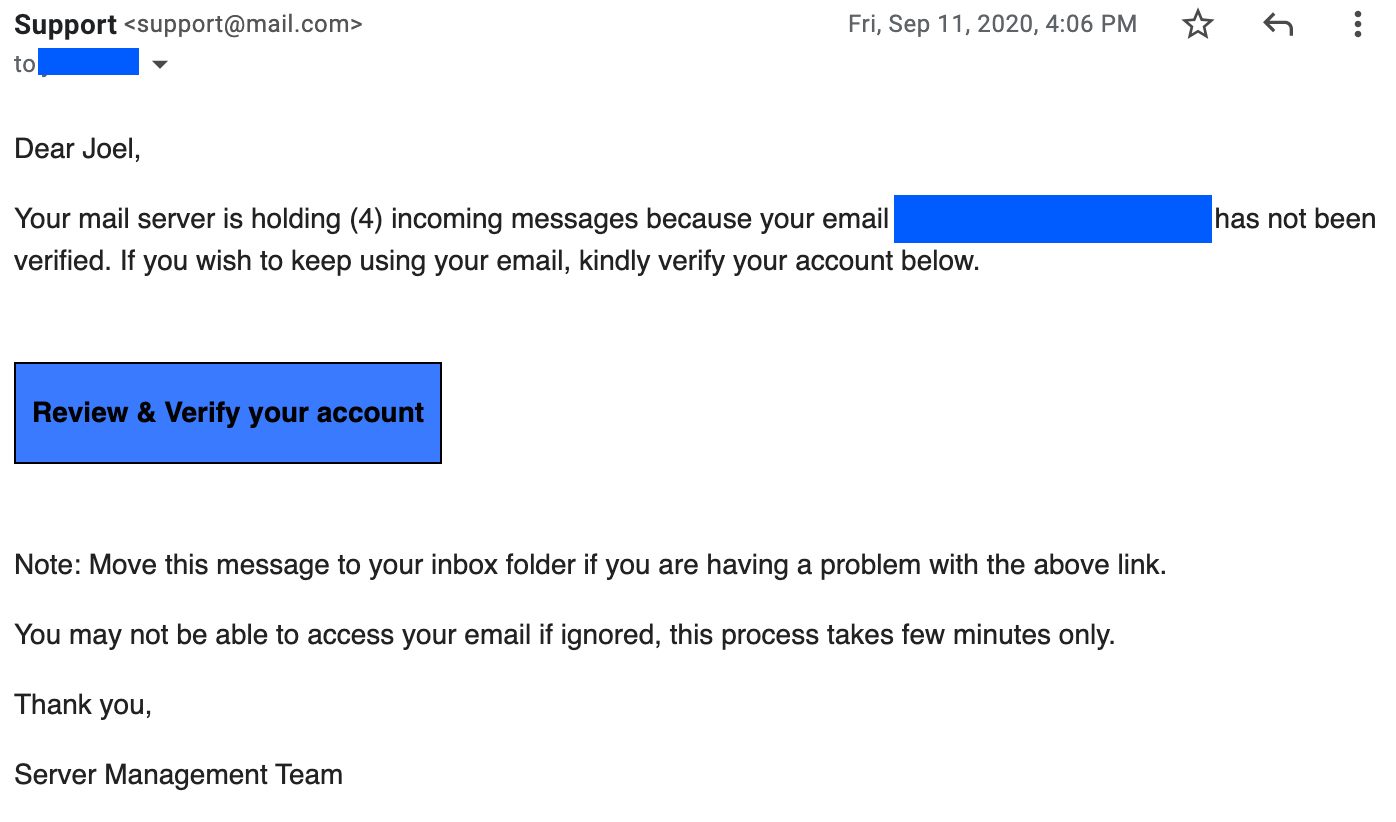
Urgency Bias
This often comes in the form of an alarming email from a supplier saying that your invoice is overdue and must be paid immediately. The hacker will conveniently include banking instructions to help speed things up.
Or just like in the email image above, the hacker can combine multiple "tools of influence" to motivate you to click that dangerous link.
Halo Effect
We tend to trust familiar brands and people we know. So what happens when a hacker makes a lookalike social media notification email? Or what about a fake package delivery email?
We've been taught to trust a lot of these types of emails, but they can just as easily be a trap...
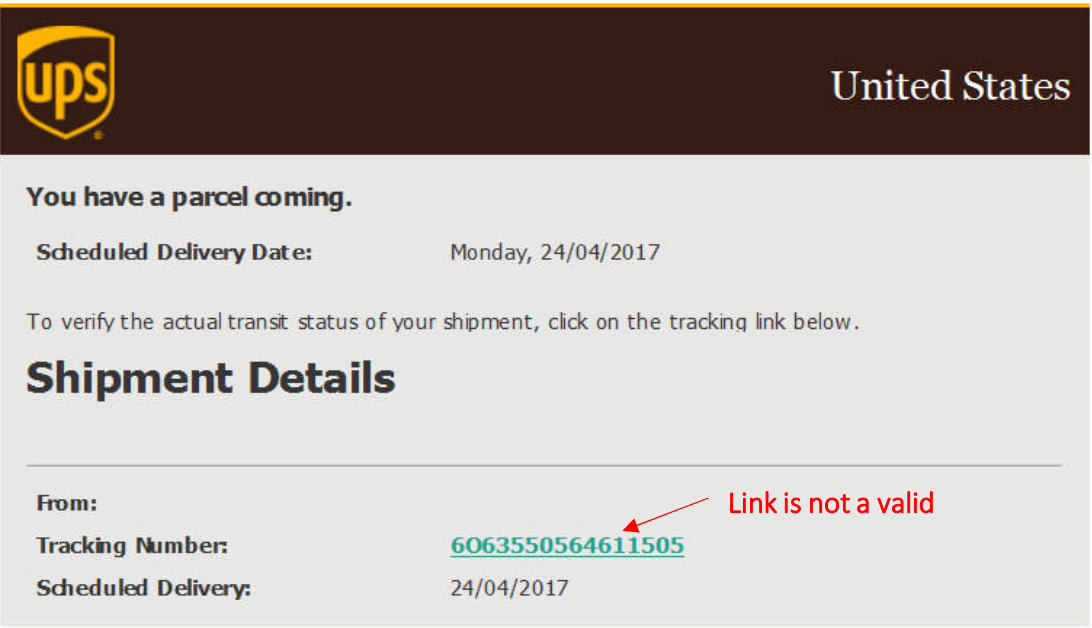
Ok let's close this up...
By fighting against the tools of influence uncovered in behavioral science, we can avoid these attacks.
That's exactly what we're doing every day at INFIMA!
We've combined cybersecurity pros with behavioral science geeks. That marriage gives you effective, Security Awareness Training for your team.
If you're an MSP and want to learn more, go check out how we work with Partners here. If you like what you see, book a time to chat!
For more examples from UPS on lookalike Phishing emails, take a look here.
[https://www.ups.com/media/news/en/fraud_email_examples.pdf]
INFIMA Security Newsletter
Join the newsletter to receive the latest updates in your inbox.






