
Using PayPal to Phish
Heads up on this one! It's shockingly effective.
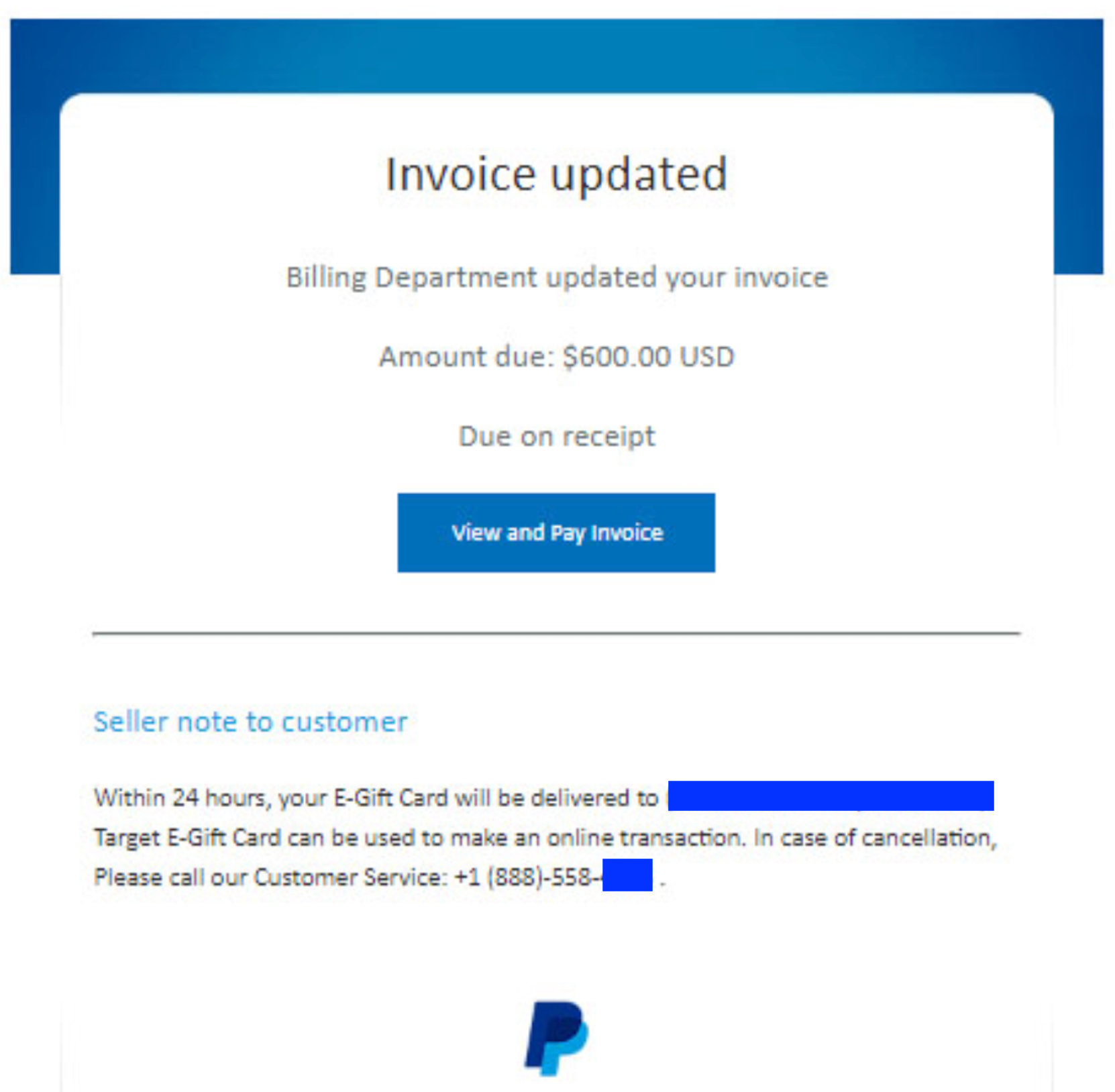
You get an email from PayPal (real PayPal) that shows an invoice for hundreds of dollars about to be drained from your account.
You perk up. You'd be crazy not to, right?!
This one is really good.
All the links in the email point back to legitimate PayPal URLs. In fact, clicking the link to "View and Pay Invoice" even brings up a real invoice inside PayPal.
So how does the hack work if the links are real?
The attacker wants you to click the links and see a real PayPal invoice. By not delivering malicious links in the email itself, this phish has a much higher rate of delivery, avoiding spam filters.
When you click the link and see this invoice, you're bound to quickly dispute the charge.
The best advice to sidestep phishing scams is to avoid clicking on links that arrive unbidden in emails... and visit the site or service in question manually — ideally, using a browser bookmark to avoid potential typosquatting sites.
Brian Krebs, krebsonsecurity.com
And yes, the hacker conveniently provides a "customer service" number. This is the behavior that the hacker is driving you toward, in order to dispute this clearly errant/fraudulent transaction.
And this is where the meat of the hack resides.
Frustrated and anxious you hurriedly call the toll-free number to resolve the issue. It's on this call that the attacker ultimately attempts to convince you to download a remote administration tool, giving the hacker unfettered access to your machine.
As always, it seems to happen so quickly.
The way to avoid this attack is to simply go directly to PayPal's site manually, NOT by clicking the link in the email. Once there, you'll see that there isn't actually any invoice in your account!
Weapons of Influence
The hackers use several weapons of influence to drive the intended behavior.
This attack leverages humans' Loss Aversion tendencies. We naturally fear a loss of something we already have more than a gain of something we don't. Just think about it - if you got an email saying you'd won $600, you'd immediately think it was a scam!
Next, the hacker nudges you to take the intended action with Urgency Bias. The email specifically states that the money will be drained from your account within 24 hours if you don't do something about it right away. False urgency forces action.
Let's add one more to the mix: Halo Effect. When something comes from a familiar brand or person, we typically trust it far more easily. PayPal has proven itself to be worthy of that trust. Unfortunately, the hacker knows this all too well. This is exactly why they've sent this email from a (presumably) compromised PayPal Business account. This makes it look completely real, and we've been conditioned to trust PayPal.
So what do you do to avoid these attacks at your organization?
Everyone knows that scams and hacks are out there, but the hackers are still making lots of money. The issue isn't knowledge; it's behaviors.
The solution is to train your people in safe online behaviors. This is exactly what we do at INFIMA.
Rooted in Behavioral Science, INFIMA focuses on removing unsafe behaviors in your team and replacing them with consistent, safe practices.
We make it easy, with a fully automated Security Awareness Training platform, built for the MSP community.
If you're an MSP and want to learn more, go check out how we work with Partners here. If you like what you see, book a time to chat!
Huge thanks to the inimitable Brian Krebs for his excellent reporting on this one.
Photo by Brett Jordan at Pexels
INFIMA Security Newsletter
Join the newsletter to receive the latest updates in your inbox.






