
Can I be hacked on my cell phone?
You hear about all the risks of Phishing attacks on your computer, but is it safe on your mobile phone?
This is a blog from a cybersecurity company, so let’s get the spoiler out of the way.
Yep - unfortunately, hackers can compromise your phone. And more.
As much as 70% of emails are opened on smartphones. Hackers know it.
With the majority of communication now done on smartphones, cybercriminals would be out of work if they didn’t figure out mobile compromise schemes.
So how do they do it?
Phishing
Email is still the primary attack vector, across the board.
In mobile Phishing schemes, the attacker doesn’t have to change anything about the look of their malicious emails. Instead, they run an immediate mobile verification check to determine whether the recipient is on mobile or not. If the victim is on a mobile phone, the attack can often be more successful.
On mobile, it’s easier for the cybercriminal to slip in malicious URLs and look-alike fraudulent websites for stealing your login credentials.
Cybercriminals have developed several ways of sneaking in fraudulent links and websites.
URL Padding
URL padding uses a known, legitimate domain but obscures the real destination by “padding” the URL with hyphens.
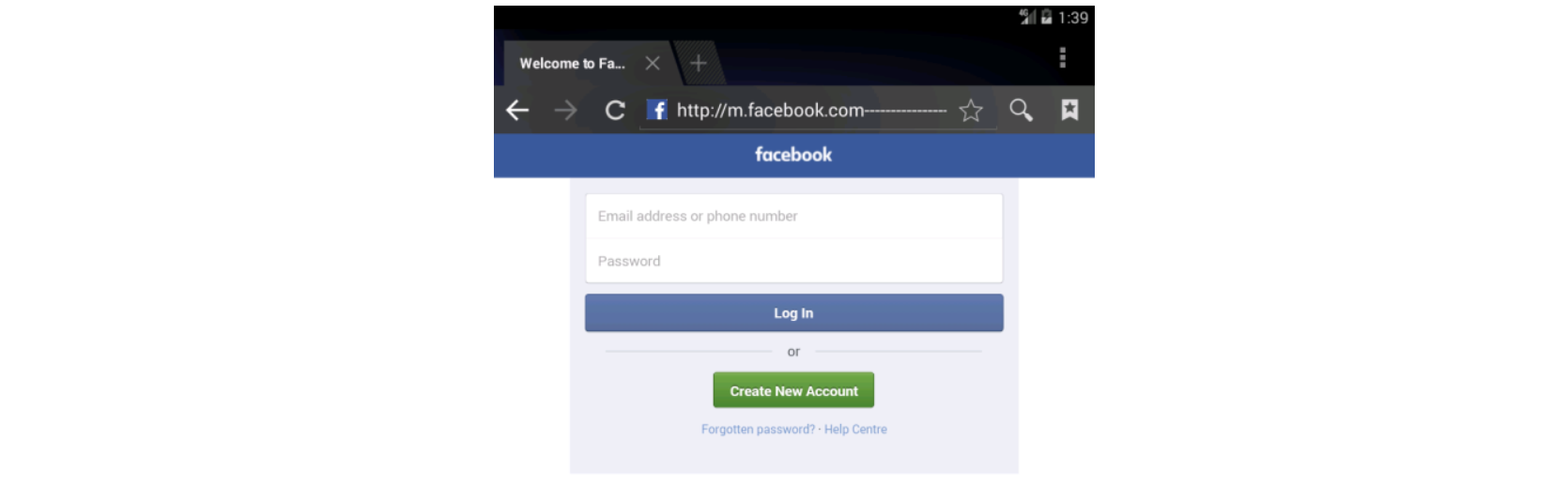
A (now defunct) real-world example used the following URL to compromise phones:
hxxp://m.facebook.com------------validate-----step1.rickytaylk[dot]com/sign_in.html
Because you’re on mobile, this sneaky attack only shows m.facebook.com in your address bar. So it seems safe, right?
Unfortunately ‘rickytaylk’ was a highly active (and successful) Phishing site.
Tiny URLs
Tiny URLs are the shortened versions of otherwise lengthy web addresses. Unlike the longer version of a domain, there’s no way to validate these domains as safe.
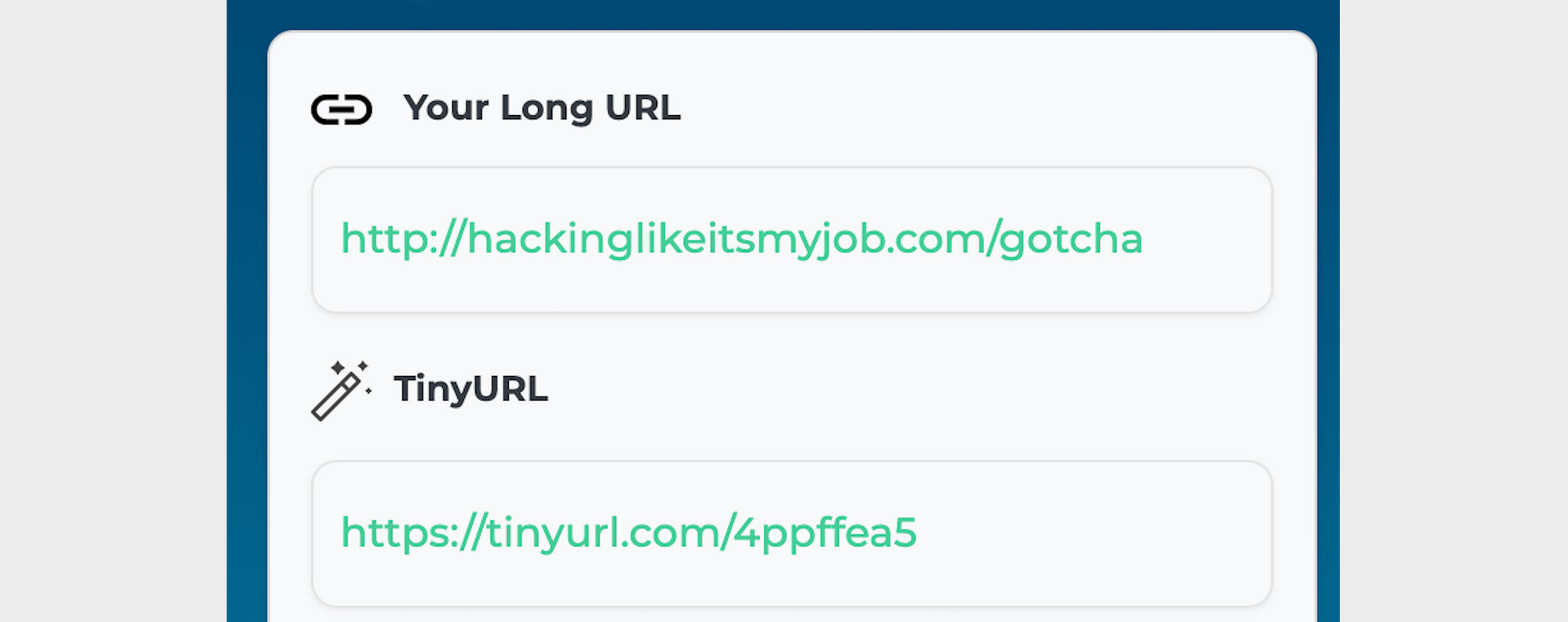
These URLs are easily created and freely distributed. They’re often the next step in an email or SMS (text message) Phishing attack.
Screen Overlay Attacks
Once an attacker knows you’re on mobile - takes a fraction of a second to do a mobile verification check - they can serve up tricky malicious mobile website and app overlays. These are very hard (or impossible) to detect.
These attacks are incredibly sneaky because the button you see is not the button you're actually clicking. They all start just the same, with a malicious email or text message.
These are just some of the ways we've seen criminals compromise phones. With more time spent on phones, it's safe to assume that hackers will develop more novel ways to break in.
How do I keep my team safe?
Your first step is to train employees on safe behaviors - at the office, at home, on the road.
Just as with any business, cybercriminal groups launch attacks where they can be most profitable. Unfortunately, many of those successful attacks now target mobile devices.
Tired of chasing down all of these attacks?
We make it easy to Train your team effectively and easily.
Consistent Security Awareness Training is one of the lowest cost, highest ROI security items in your arsenal.
Start with a quick quote - hit us up
